TECHNOLOGY
July 8, 2025
Saurav Dhawale
Navigating the VDI Landscape: A Strategic Guide Post-VMware Acquisition Navigating the VDI Landscape: A Strategic Guide Post-VMware Acquisition ​ While VMware has long been the go-to vendor for virtualization technologies, its recent acquisition by Broadcom has stirred doubts amongst...
July 8, 2025
Saurav Dhawale
Implementing edge-to-cloud networking security: A best practice brief Implementing edge-to-cloud networking security: A best practice brief ​ Users are accessing your network from virtually everywhere— to reach applications that are hosted in the cloud, onsite, and from third parties....
July 8, 2025
Saurav Dhawale
Imaging Innovation: Digital Imaging solutions for Limitless Creative Possibilities Imaging Innovation: Digital Imaging solutions for Limitless Creative Possibilities ​ In the ever-evolving realm of digital imaging, it is imperative for users of the Sony SDK to remain abreast of the...
July 8, 2025
Saurav Dhawale
Navigating Hypervisor Migration: Veeam’s Effortless Approach
July 8, 2025
Saurav Dhawale
Ihr Schlssel zum KI-Erfolg? Vertrauenswrdige Daten Ihr Schlssel zum KI-Erfolg? Vertrauenswrdige Daten ​ KI-basierte Analysen verbessern Geschäftsabläufe, fördern Innovationen und verändern das Kundenerlebnis. Sie sind jedoch nur so gut, wie die Daten, von denen sie gespeist werden....
July 8, 2025
Saurav Dhawale
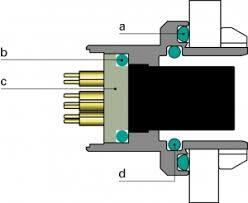
Navigating Engineering Hurdles: Sealed Connectors In Harsh Environments
July 8, 2025
Saurav Dhawale
Identity Security for Software Development Identity Security for Software Development ​ We wrote this book for developers, engineers, or anyone who isn’t afraid of a little code, but anyone looking to understand how secure software is built can enjoy it. Evolving technology and industry...
No posts found
Recent Posts
Introduction In today’s fast changing B2B world, businesses require more than traditional marketing...
Introduction: Why B2B leader in the main generation 2025 B2B lead generation trends for 2025 are transforming...
Top Strategies to Secure Your Freight and Prevent Cargo Theft Sponsored content for AMAROK by studioID...
Optimizing for Growth: Ørsted’s Journey to a Modern ETRM Solution Sponsored content for PCI Energy...
Digital Twins: How Transparent City Planning Builds Trust Digital Twins: How Transparent City Planning...
Accessible Design: The Key to Customer Loyalty and Sales Accessible Design: The Key to Customer Loyalty...
How to help students avoid the career readiness gap How to help students avoid the career readiness gap...
Your Cotton Leaves Hold Untapped Power Sponsor Content Presented By PhycoTerra® Your Cotton Leaves Hold...
Replacing your current cloud phone with Zoom Phone is as easy as 1-2-3 Replacing your current cloud phone...
How AI-powered phones are changing the modern workplace How AI-powered phones are changing the modern...
Zoom Workplace vs. Microsoft Teams Zoom Workplace vs. Microsoft Teams Organizations need a seamless collaboration...
The Case for Application Detection and Response (ADR) The Case for Application Detection and Response...
No posts found