SECURITY
December 10, 2025
prathmesh kupade
Cybersecurity is extra critical than ever as digital threats boom every year. By 2025, companies and individuals will face threats along with ransomware assaults, phishing scams, identification robbery and account hacking. As more and more human beings ask what cyber protection is and how they could...
December 10, 2025
prathmesh kupade
What Is AI & Best AI Tools
Understanding Artificial intelligence, gaining knowledge of What is AI, and using cutting-edge AI equipment are actually crucial in commercial enterprise, education, content advent, and ordinary life. AI is not futuristic—it is a sensible, reachable era improving productivity,...
September 30, 2025
Saurav Dhawale
Software Under Siege 2025
Software Under Siege 2025
Your applications are under attack like never before.
Contrast’s 2025 Application Threat Report reveals...
May 24, 2025
Saurav Dhawale
What Is Cybersecurity Threat Intelligence?
Cybersecurity Threat Intelligence refer to the collection, analysis and spread of information on today’s and potential cyber threats. This helps intelligence organizations to estimate, prevent and respond to cyber attacks more efficiently.
This involves...
March 25, 2025
Arken
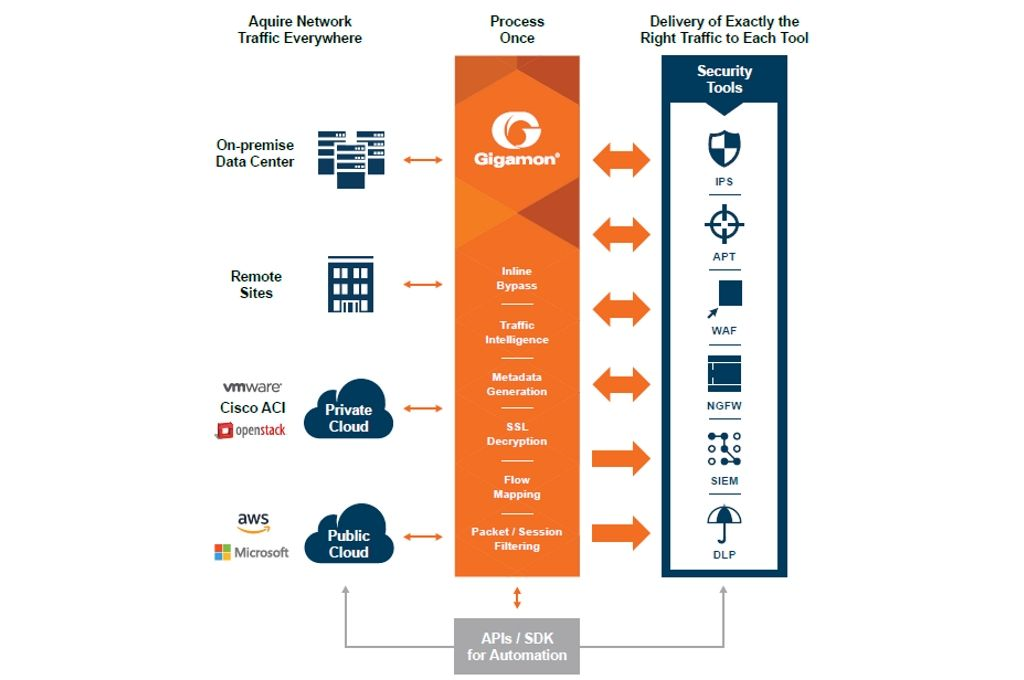
Read “Security at the Speed of Your Network” to learn why organizations are using an architectural approach to improve security posture and reduce costs. Secure higher traffic volumes on networks up to 100G with no compromise between security, performance and cost. Read now.
March 24, 2025
Arken
Read “Security Delivery Platforms for Dummies” to transform how security and monitoring tools are deployed for better performance. Detect threats faster by removing network blind spots, monitor what is happening across the global enterprise and increase the effectiveness of your security tools.
March 23, 2025
Arken
Upgrading your network doesn’t have to be a big headache. Get the Securosis report Scaling Network Security and discover your options for improving security architecture on your terms, using existing infrastructure and intelligently applying security controls at scale without major overhauls.
No posts found
Recent Posts
The future of digital advertising is smarter, faster, and further automated than ever in advance than....
Why Google Ads Matters for B2B Tech Publishers
Google Ads is one of the maximum effective acquisition...
Cybersecurity is extra critical than ever as digital threats boom every year. By 2025, companies and...
What Is AI & Best AI Tools
Understanding Artificial intelligence, gaining knowledge of What is...
What is ABM Marketing?
Account-based totally advertising (ABM) is a hyper-targeted B2B increase strategy...
Why CRM Software Matters in 2025
Marketing teams today handle thousands of potential customers across...
1. What is ABM marketing?
In B2B marketing, ABM marketing (account-based marketing) is a strategic...
Introduction
In today’s fast changing B2B world, businesses require more than traditional marketing...
Introduction: Why B2B leader in the main generation 2025
B2B lead generation trends for 2025 are transforming...
Digital Twins: How Transparent City Planning Builds Trust...
Accessible Design: The Key to Customer Loyalty and Sales...
How to help students avoid the career readiness gap...
No posts found